Database Security and Authorization Subsystem
보안 및 권한부여
DB security
- legal and ethical
- policy issues
- system-related issues
- security levels
Threats to Databases
- Loss of integrity : 무결성 상실
- Loss of availability : 가용성 상실
- Loss of confidentiality : 기밀성 상실
access control, inference control, flow control, encryption
DB security : not an isolated concern
- multiuser DB system
- database security and authorization subsystem : 보안 및 권한부여 하위시스템
- Discretionary : 임의적 보안 메커니즘
- Mandatory : 강제 보안 매커니즘
Control measures
- Access control : 접근제어
- Inference control : 추론제어
- Flow control : 흐름제어
- Data encryption : 암호화
Access control : 로그인 제어
Inference control : 통계 DB에 대한 보안 (statistical DB)
Flow control : covert channels (불법 비밀경로)를 막기 위해
Data encryption : 네트워크 전송시 민감 데이터 보호
DBA’s responsibilities
granting pricileges to users : 권한 부여
classifying users and data : 유저 및 데이터의 분류
- account creation → access control
- privilege granting → discretionary control (재량 제어)
- privilege revocation → discretionary control (재량 제어)
- security level assignment → mandatory control (의무 제어)
Access protection and DB audits : 접근 보호와 DB 감사
- account number and pw
- system log : recovery data, user acct, device ID
- 모든 작업을 추적
- DB 감사 : audit trail (감사 추적) - 주로 보안 목적의 log
Discretionary Access control based on Granting and Revoking Privileges : 임의접근 제어
권한부여 식별자 authorization = user = account
two level for assigning pricileges to use the DBS
- the account level : 각 계정의 db와의 관계 및 권한을 지정
- the relation level : db의 개별 관계나 보기에 접근할 수 있는 권한 제어
The privileges at the account level

privileges at the relation level
defined for SQL2
Access matrix model
- authorization table : 권한부여 테이블

Grant and Revoke mechanism : 권한 주기 및 뺏기
→ Grant 권한 [On object] To users
[With Grant Option] : 권한을 다른 유저에게 줄 수 있음
→ Revoke 권한 [On object] From users
view에 대한 권한 : 업데이트/삽입은 특정 속성만 권한주기 가능 but 삭제 및 선택 권한은 따로 지정하려면 view 사용해야함
Mandatory Access Control and Role Based Access Control for multilevel security : 강제접근권한과 역할기반 접근 제어
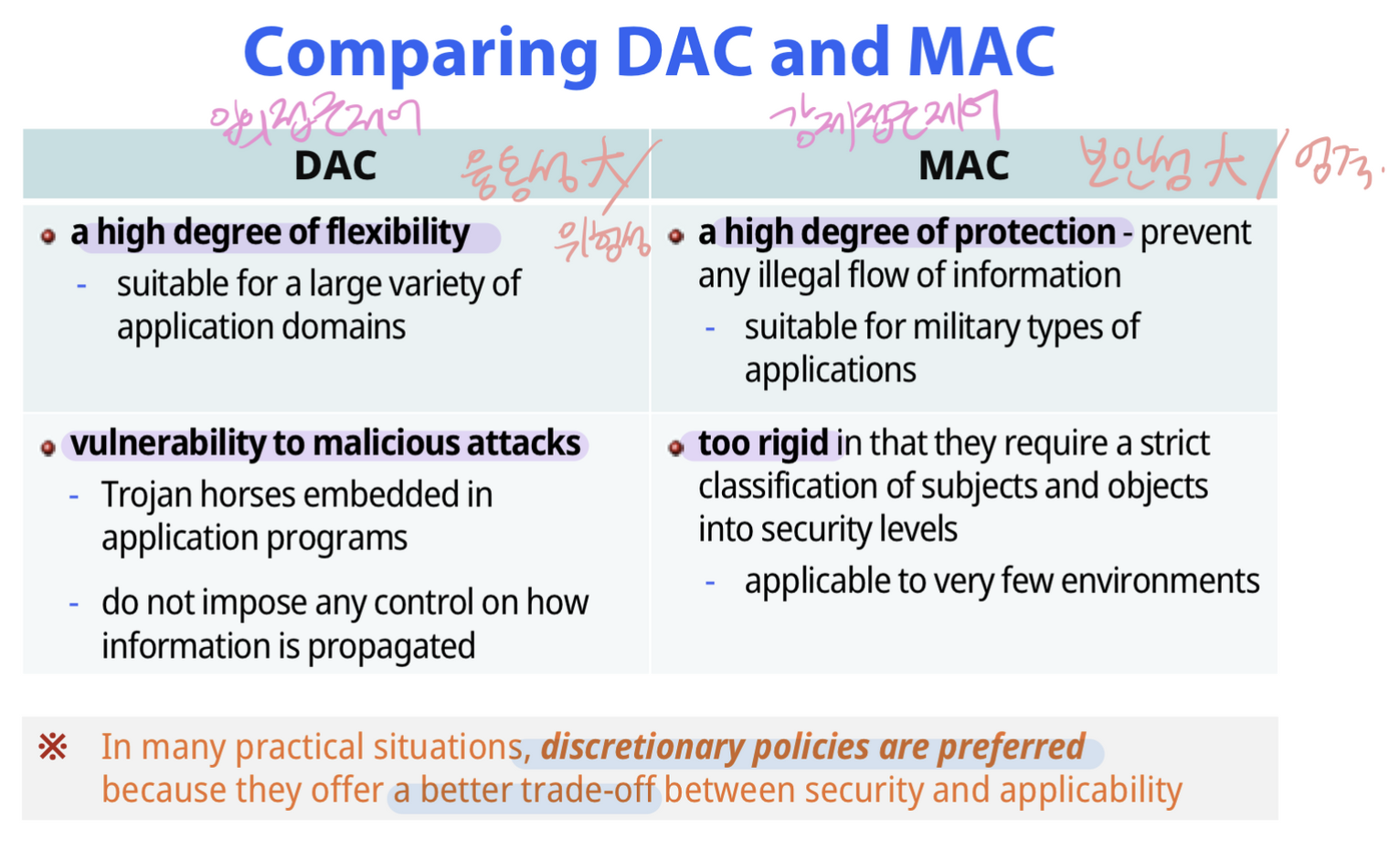
Discretionary access control (DAC)
- granting and revoking privileges
- all or nothing method
Mandatory access control (MAC)
- 분류 후 멀티레벨 보안기법
Data Classification Scheme : 데이터 분류 기법
- independent control
- data classification level (security classes)
- TS > S > C > U
- user clearance level : 동일
- 정보레벨 매칭을 통한 보안기법
the Bell-Lapadula Model
class(S) : subject S (user level)
class(O) : object level
restrictions
- 유저레벨 ≥ 객체레벨 : 읽기 가능
- 유저레벨 ≤ 객체레벨 : 쓰기 가능 (원래 데이터의 레벨을 낮출 수 없게)

Role-Based access control
RBAC : 규모가 큰 시스템을 관리
- permissions are associated with roles, and users are assigned to appropriate roles
- CREATE ROLE and DESTROY ROLE commands
- RBAC can be used with DAC, MAC
- 지정된 역할에 있는 권한 있는 사용자만 특정 데이터 또는 리소스에 대한 액세스 권한을 가집니다.
Treats to a DB system
- SQL injection : SQL 주입
- Unauthorized privilege escalation : 무단 권한상승
- Privilege abuse : 권한 남용
- Denial of service (DOS) : 서비스 거부
- Weak Authentication : 취약한 인증
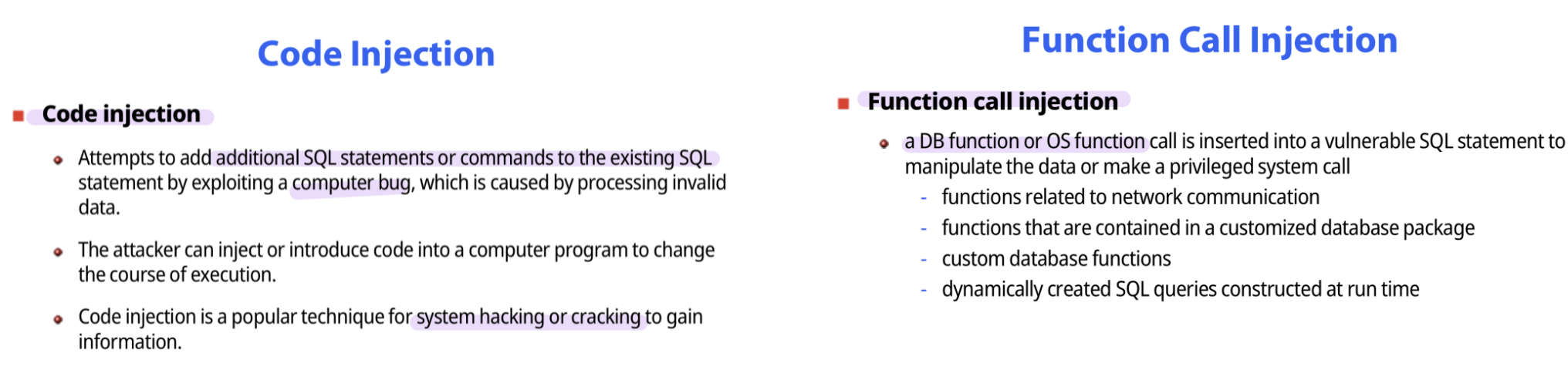
SQL injection methods
sql 에 string을 주입해서 상태를 변경
manipulation attack, code inject, function call inject

Risks associated with SQL injection : 위험 요소
- DB 핑거프린팅
- 서비스 거부
- 인증 무시
- 주인가능한 파라미터 식별
- 원격 명령실행
- 권한 상승 수행
Protection techniques against sql injection
- Bind Cariables (using parameterized statements)
- Filtering Input (input validation)
- Function Security
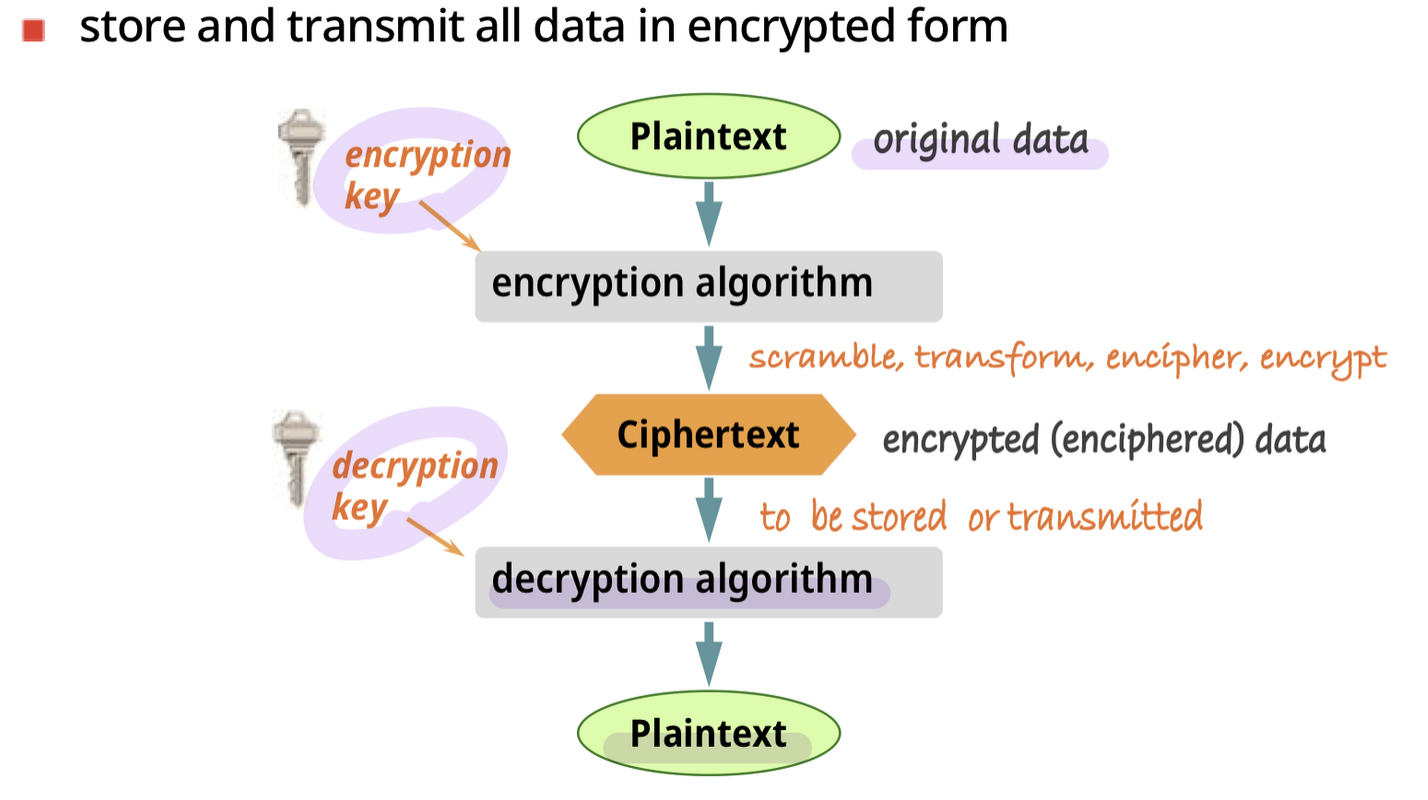
Data encryption : 암호화
Data Encryption Standard : DES
provide end-to-end encryption between the sender and receiver
hybrid scheme of
- substitution procedure : 대체 암호화 키
- permutation : 일반 문자를 재정렬
for 16 cycles
hw or sw
Block encryption technique
divide text into 64 bit blocks of plaintext
56-bit number
AES : Advanced Encryption Standards
- can use keys of 128, 192, 256 bits
Symmetric Key Algorithms
a secret key algorithm
내용 암호화
Public (Asymmetric) Key Encryption
- encryption key : public(open) key
- decryption key : private (secret) key
- 해독키를 가지고 암호키 추론 = 가능
- 암호키로 해독키 추론 = 불가능
the RSA public key Encryption Algorithm
- RSA scheme : 사람 이름을 땀
- 프라임 넘버 & 소인수분해 이용

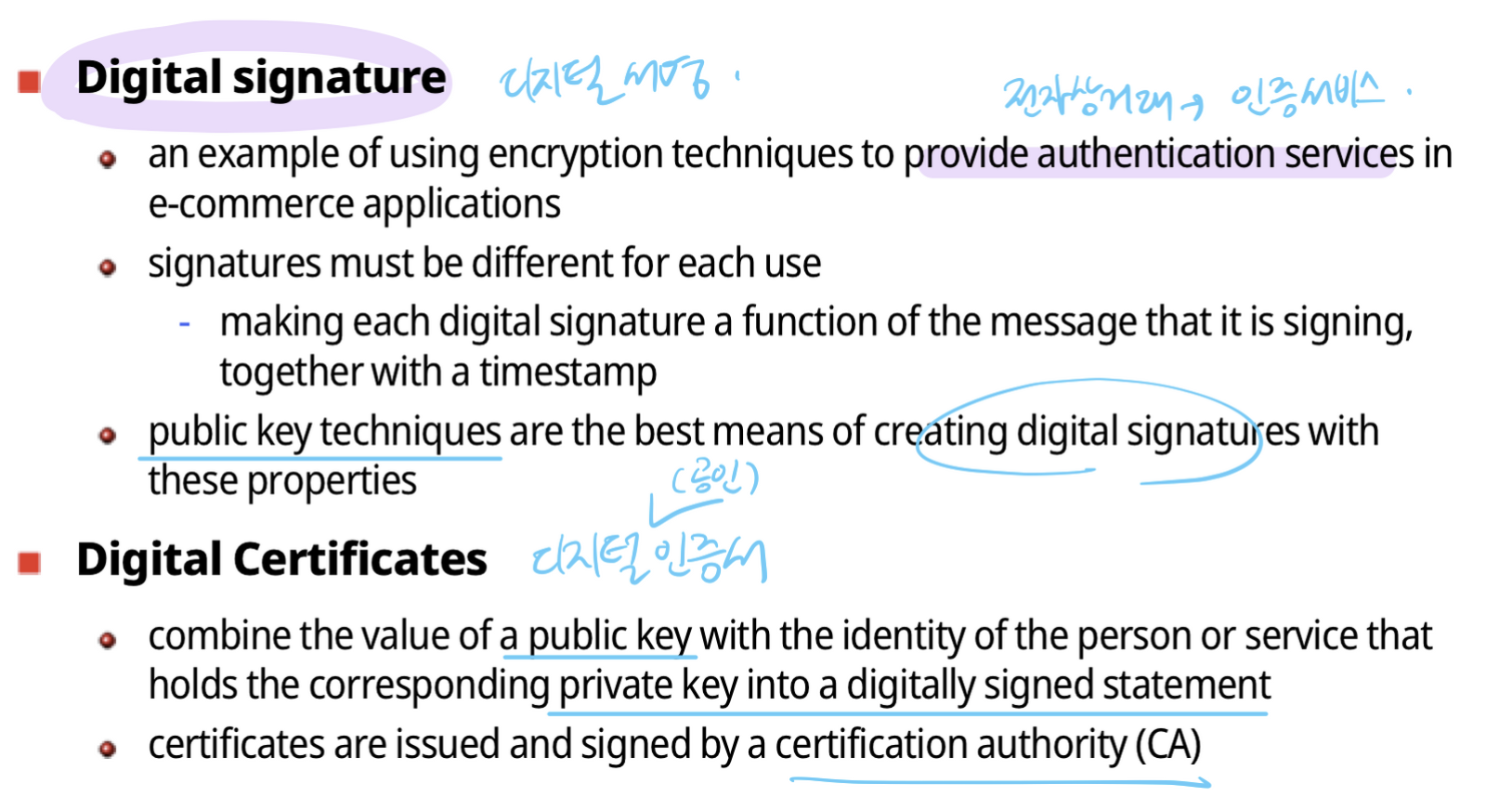
Digital signature and Certificates : 디지털 서명과 인증서
'📚 전공 공부 > DB기초' 카테고리의 다른 글
| [SQL] mysql 내장함수 정리 (0) | 2023.03.03 |
|---|---|
| [SQLD] 전공자 sqld 시험 후기/ 준비방법/ 공부 (0) | 2023.01.16 |
| [DB] 데이터베이스 복구 (0) | 2022.12.30 |
| [DB] 동시성 제어 (0) | 2022.12.30 |
| [DB] Transaction processing (0) | 2022.12.30 |


